Background
Based on the latest beta builds, Apple has added OAuth 2.0 support for Microsoft Exchange accounts in iOS 11, showing an increased commitment to device security. In my opinion, this may be iOS 11’s least talked about, but most impactful feature for enterprises because of the implications for securing iOS with Office 365 and Exchange Online. Let’s dig deeper.
A Brief History on Securing Exchange ActiveSync
Prior to iOS 11’s OAuth 2.0 implementation, ActiveSync email clients such as iOS’s native email handled account authentication to Exchange Online exclusively via something called an Active Profile. The Active Profile defines ActiveSync authentication techniques for non-browser or modern authentication-based clients.
On-premises Microsoft Exchange servers are deployed on secure networks behind layers of firewalls and only accessible to email clients through ActiveSync Proxies. Administrators have significant granular access control via proxies, especially in allowing access to the Exchange servers only from the trusted IP addresses of the proxies. MobileIron’s Sentry is an extra-powerful ActiveSync proxy for mobile devices because the Sentry allows or denies ActiveSync access to the Exchange server based on both device and application posture received from the policy engine on MobileIron Core or Cloud. With Sentry, only trusted mobile devices can access ActiveSync email; users attempting to access email from untrusted mobile devices are denied by the Sentry. Thousands of large enterprises protect their on-premises Exchange servers with Sentry today.
Office 365 complicates things for administrators because the email servers live in the cloud, presenting the challenge of securing access to a service that is outside the company’s trusted network. In the past, basic authentication (user & password) was the only option for the Active\ Profile when authenticating to Office 365 ActiveSync email. The ActiveSync email client’s authentication request and credentials are sent to Office 365 first. Office 365 then acts as an authentication broker for the ActiveSync communication. It determines the client’s federated domain and then brokers the authentication connection with an Identity Provider (IdP) such as Microsoft’s ADFS. This transaction flow is illustrated in the image below:
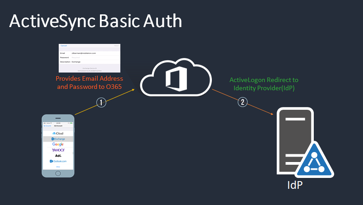
In this deployment model, limiting Office 365 ActiveSync to only compliant devices is more complicated. MobileIron customers commonly use MobileIron Sentry with IP-based federated claims rules within their IdP. In these deployments, the Sentry still acts as an ActiveSync proxy for managed clients and administrators simply add IP-based claims rules restricting authentication to transactions coming only from the Sentry IP address(es). The Sentry enforces access to email from only compliant devices; the claims rules prevent users from bypassing the Sentry and connecting directly to Office 365 email.
Office 365 CBA for ActiveSync
Last year, in an effort to simplify authentication to Office 365, Microsoft announced certificate-based authentication (CBA) support for Office 365 ActiveSync and modern authentication clients such as Microsoft Office applications. Microsoft defines modern authentication “through their Active Directory Authentication Library (ADAL)-based sign-in to Office client apps across platforms. This enables sign-in features such as Multi-Factor Authentication (MFA), SAML-based, third-party Identity Providers with Office client applications, and smart card and certificate-based authentication. It also removes the need for Outlook to use the basic authentication protocol.”1
With Office 365 CBA for ActiveSync, administrators deploy an ActiveSync profile that includes a certificate for user authentication via an EMM such as MobileIron, instead of a username and password. The email application communicates directly with Exchange Online; users are validated against a publicly trusted and published certificate revocation list (CRL) from the certificate authority (CA).
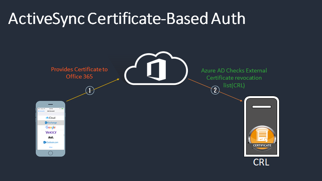
For more information on leveraging CBA for Office 365 with MobileIron, please see the following links below (requires MobileIron Community account):
Federation and the Future of Services
One of the most limiting factors of the Active Profile authentication techniques just outlined is that it requires the client to present the credentials to a cloud service that is outside of the control of the enterprise. With Office 365 ActiveSync authentication, user credentials (basic or certificate) are sent directly to Microsoft’s Azure AD cloud service for authentication. Many enterprises have trepidations about storing identity in the cloud, and almost all enterprises now need to authenticate users to multiple cloud services without having to replicate their identity stores over and over. Enter the standards-based Identity Provider (IdP), an authentication service based on standards such as SAML, OpenID Connect, OAuth, and/or WS-Federation through support of modern and/or passive authentication. In a passive authentication flow, the user signs in through a browser-based client where they are redirected to their Identity Provider(IdP) for authentication.
By leveraging an IdP, users authenticate with the IdP instead of directly to each cloud service. Additionally, by using an IdP, advanced requirements such as single-sign on (SSO) and multi-factor- authentication (MFA) are possible.
What Does This Have to do with iOS 11 and Native Email?
In iOS 11, the native email client now supports user authentication via OAuth 2.0, but only for user-driven account creation. The positive side of this feature is that iOS 11 end-users can authenticate their email directly with their IdP using passive authentication, perhaps leveraging MFA. We will do a more technical deep dive in a future post. The following embedded video demonstrates the end-user experience when adding an Exchange Online account:

The downside? This is strictly a user-drivenfeature, at least for now. Apple has exposed NO MDM primitives in iOS 11 that let an EMM configure the email client to use the new OAuth2 feature. Administrators are still limited to the traditional active profile configuration when provisioning an Exchange profile. But there’s more to be concerned about.
Exchange Online Security Concern
The new user-driven iOS 11 email account creation feature means that administrators have lost much of the security controls they may have in place. For example, user-created email accounts can now bypass any IP-based claims rules set to block untrusted ActiveSyncconnections. The administrator thus loses many of the access and enforcement controls they depend on. Since these user-created accounts are unmanaged, the administrator loses DLP controls so end-users can retrieve email and open attachments with unsecured apps and cloud services. The following video compares traditional techniques such as claims rules restricting Exchange Online accounts in iOS 10.3.3 with iOS 11’s new OAuth 2.0 account creation.
What should be obvious by now is that the trend towards cloud services changes how users authenticate and how administrators secure access to those services. Browser-based and/or native application authentication requires a new approach to ensure users are accessing services from a compliant device AND compliant application(s).
Securing Office 365 and the Future of Authentication with MobileIron Access
MobileIron Access ensures that only compliant devices and applications can authenticate with your IdP and access secured services. The integration between IdP and MobileIron Access is through leading standards-based protocols such as SAML 2.0 or WS-Federation. As a result, MobileIron Access can secure all the leading cloud (and on-premises services) without the need for special SDKs or wrappers. MobileIron Access includes granular conditional access rules that empower administrators to block an end-user from manually adding their Office 365 account, thus mitigating the Apple-introduced iOS 11 issue we’ve just explained. The following screen-shot from MobileIron Access illustrates some pre-configured conditional access capabilities administrators need:
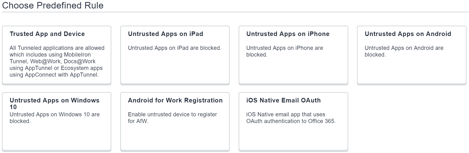
MobileIron Access doesn’t just block the user through these granular conditional access rules. The administrator can also send the end-user to customizable remediation pages based on the conditional access rule set.
End User Experience
MobileIron’s operating thesis has always been to provide end-users with choice and the native device experience, while still providing all the necessary security controls administrators need. The following video shows how an end-user goes from non-compliant to secure, seamless experiences in just a few screens when attempting to access their email on an iOS 11 device.
There are a lot of moving parts in this video, so let’s break down what happens behind the scenes:
- First, a user attempts to add an Exchange Online account on an unregistered device. Through MobileIron Access’ customizable compliance page, the end-user is asked to enroll their device before being allowed to access email.
- Next, the end-user is redirected to a recognizable screen, their company’s IdP, to enroll in MobileIron.
- After authenticating, the enrollment process provisions the device with all the configurations, policies, end-user privacy controls, and line of business applications defined by the enterprise.
- The user’s Exchange Online email account profile is seamlessly added and verified using certificate-based authentication. This exchange account is under administrative control and leverages native iOS DLP controls to keep email and email attachments within the confines of trusted and managed applications while protecting these critical data from leaking into uncontrolled contexts like personal applications.
- When the user selects an approved and managed Line of Business application on the device (e.g. Microsoft Word and Salesforce1), they are seamlessly authenticated to the service through MobileIron Access without having to manually enter credentials.
- Lastly, the end-user installs a personal application in an attempt to access their salesforce account. Through MobileIron Access’ customizable compliance page, the end-user is asked to use the applications specified by company policy and is provided a link to learn more about their terms and conditions.
In summary, the end-user is provided an easy workflow to make their device compliant with enterprise policies so that they can easily and securely access their work email using iOS native email client.
MobileIron Recommendations
Of course, we’re hoping that this new iOS 11 email feature becomes configurable through MDM controls in the future. As we’ve seen though, MobileIron Access provides powerful conditional access capabilities along with the customizable remediation page that mitigates this iOS 11 limitation. We recommend customers look into using the conditional access rules to allow only managed email accounts provisioned by MobileIron to access their Exchange Online accounts. Using the configurable remediation page along with this rule, administrators can direct users to register their devices with MobileIron so they that can enjoy seamless authentication to Office 365, including Exchange Online and so that the enterprise’s assets can be properly secured.
For those that need to go deeper, we’ll go into more technical details and present alternatives in a future post. Stay tuned.
1 "Using Office 365 modern authentication with Office clients - Office 365."
https://www.mobileiron.com/en/smartwork-blog/practicing-safe-security-ios-11-and-office-365