Whilst prepping our WS1 lab environment for an upgrade, it was found that Android devices enrolled and was manged correctly but Apple devices had no APNs push, they would enrol and check in but not receive and profiles or apps.
After changing the APNs certificate for that LG, we still had the same issue, digging deeper and looking in to the DB with select * from dbo.APNsGenerationStatus showed the APNs certificate correct in the DB.
from both the Console Server and Device server ‘telnet gateway.push.apple.com 2195’ and’ telnet feedback.push.apple.com 2196’ connected.
Using Wireshark we found a TLS1.2 handshake error
This related to port 2195
TLSv1.2 Record Layer:Alert (Level Fatal, Description: Handshake failure)
On the console and device server only TLS1.2 was enabled and weak TLS_RSA_WITH_AES cyphers were disabled.
Qualys SSL Labs report gave the device server a grade A and the Console server a grade A+
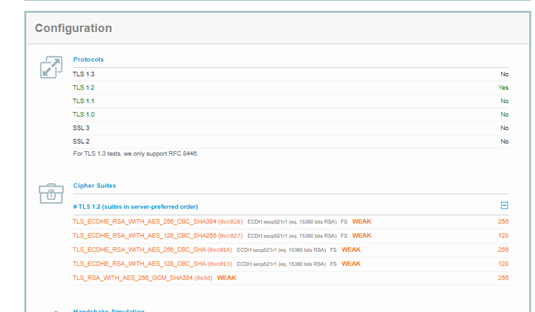
enabling the following cyphers on the Console server cured the TLS hand shake errors:
| TLS_RSA_WITH_AES_128_GCM_SHA256 (0x9c) WEAK | 128 |
|---|---|
| TLS_RSA_WITH_AES_256_CBC_SHA256 (0x3d) WEAK | 256 |
| TLS_RSA_WITH_AES_128_CBC_SHA256 (0x3c) WEAK | 128 |
| TLS_RSA_WITH_AES_256_CBC_SHA (0x35) WEAK | 256 |
| TLS_RSA_WITH_AES_128_CBC_SHA (0x2f) WEAK | 128 |
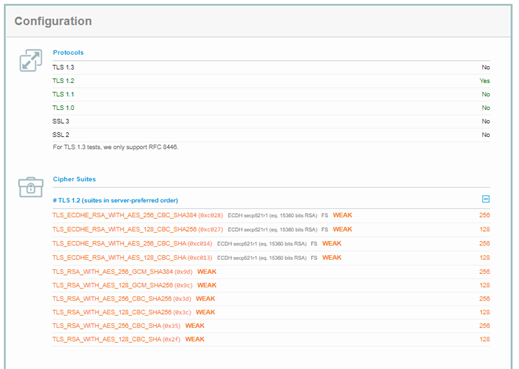
The CBC ciphers are deemed to be weak and recommended to be disabled, however you will block APNs push if you do.
This article is very useful.
This refers to handshake errors and gateway.sandbox.push.apple.com:2195
An interesting exercise.