Recently I’ve had to build configurations via Intune to limit the users that could log into an AAD only joined machine.
AAD itself does not provide controls around limiting user login into specific machines hence I had to apply controls via Intune.
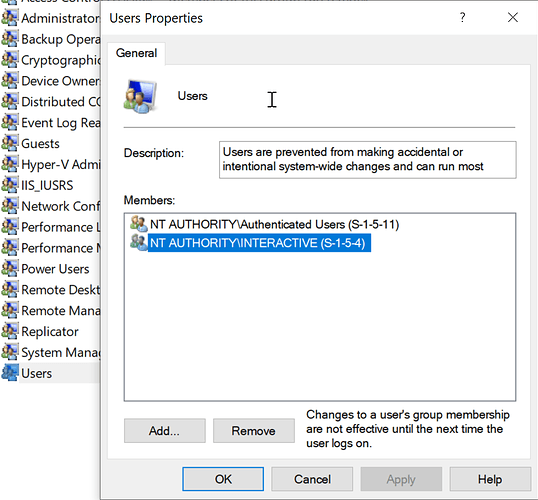
Windows 10 Users local group allows NT Authority\Authenticated Users to log into the machine which is every Azure AD user
I’ve had to make changes to this local group via Intune in order to remove NT Authority\Authenticated Users and add the list of Azure AD users that I wanted to be able to log into the machine.
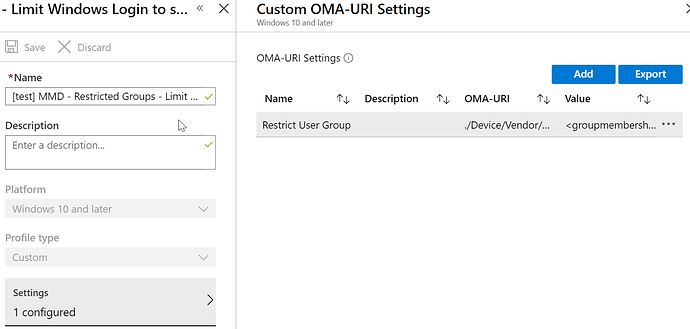
This was achieved via the use of “Restricted Groups” which are documented by Microsoft here:
Restricted groups takes over the management of the local group effectively removing any members that are not specified in the policy configuration.
The configuration that I’ve used is below:
| Name | Value |
|---|---|
| OMA-URI | ./Device/Vendor/MSFT/Policy/Config/RestrictedGroups/ConfigureGroupMembership |
| Data Type | String |
Value:
<groupmembership>
<accessgroup desc = "Users">
<member name = "AzureAD\user1UPN@yourdomain.com" />
<member name = "AzureAD\user2UPN@yourdomain.com" />
<member name = "AzureAD\user3UPN@yourdomain.com" />
<member name = "AzureAD\user4UPN@yourdomain.com" />
<member name = "NT Authority\INTERACTIVE" />
</accessgroup>
</groupmembership>|
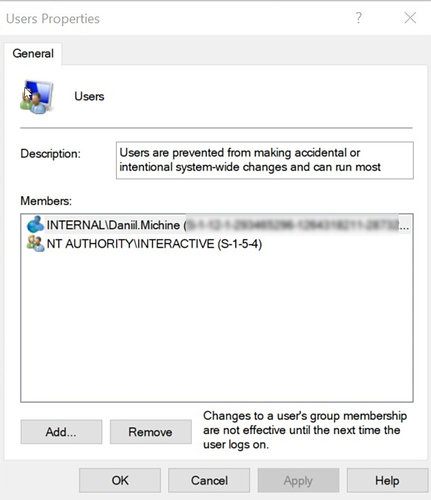
The above configuration has removed NT AUTHORITY\Authenticated Users from the Users group and have added the specified users