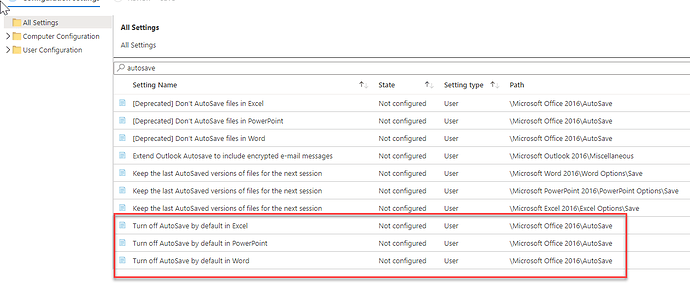
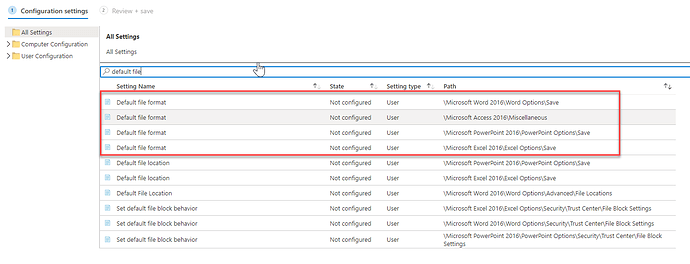
Intune provide capability for deploy policies that are no displayed via the GUI by ingesting and applying group policy.
This works by first installing the group policy ADMX on the machine and then applying the changes specified in ADMX.
However I’ve come across a number of issues while ingesting ADMX files and had to figure out the trobuleshooting steps.
Policy ingestion steps and the problem
Here is an example of Office ADMX ingestion and some issues I’ve run across the way.
Microsoft doc on ingestion below
First step is to download and extract the Office ADMX file
https://www.microsoft.com/en-us/download/details.aspx?id=49030
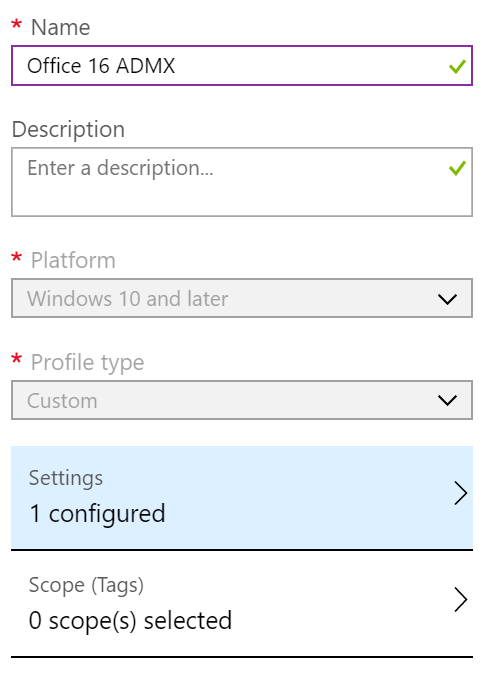
Second step is to create a custom Windows 10 profile
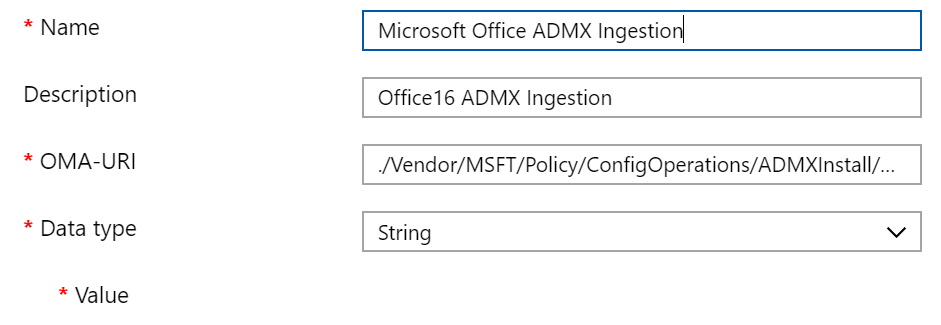
With the following configuration
OMA-URI: ./Vendor/MSFT/Policy/ConfigOperations/ADMXInstall/Office16/Policy/Office16Policy
Open office16.admx and copy the content into the value field.
Save and assign the policy.
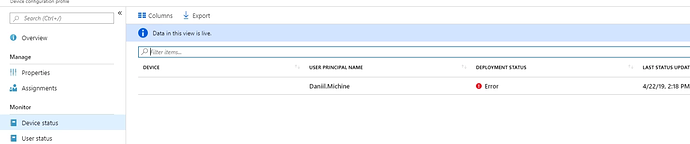
After the policy assignment deployment has failed
Troubleshooting steps
Intune policy pushes are recorded in the following event log
Microsoft-Windows-DeviceManagement-Enterprise-Diagnostics-Provider/Admin
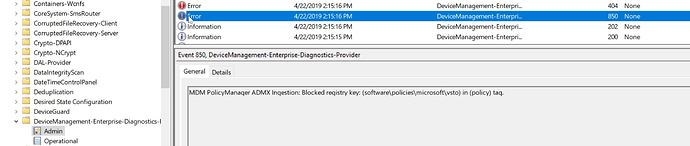
Looking at the event log I’ve noticed the following error
Looks like there is a problem with software\policies\microsoft\vtso registry key
Quick Google search (Support Tip: Ingesting Office ADMX-Backed policies using Microsoft Intune - Microsoft Community Hub) reveals that the following keys cannot be modified in this way
- software\policies\microsoft\vtso
- software\policies\Microsoft
Upon finding this I’ve had to modify the value in Intune policy and remove the following keys
<policy name="L_EnableMinimizeVbaResigning" class="User" displayName="$(string.L_MinimizeVbaResigning)" explainText="$(string.L_MinimizeVbaResigningExplain)" key="software\policies\microsoft\vba\security" valueName="minimizevbaresign">
<parentCategory ref="L_SecuritySettings" />
<supportedOn ref="windows:SUPPORTED_Windows7" />
<enabledValue>
<decimal value="1" />
</enabledValue>
<disabledValue>
<decimal value="0" />
</disabledValue>
</policy>
<policy name="L_DisableVSTOLegacy1Or2" class="User" displayName="$(string.L_VSTOLegacy1Or2)" explainText="$(string.L_VSTOLegacy1Or2Explain)" key="software\policies\microsoft\vsto" valueName="vstolegacy1or2disable">
<parentCategory ref="L_SecuritySettings" />
<supportedOn ref="windows:SUPPORTED_Windows7" />
<enabledValue>
<decimal value="1" />
</enabledValue>
<disabledValue>
<decimal value="0" />
</disabledValue>
</policy>
Once this was done the ADMX has successfully installed