I’ve had reports of issues with users attempting to access surveymonkey.com.
Following error messages are seen:
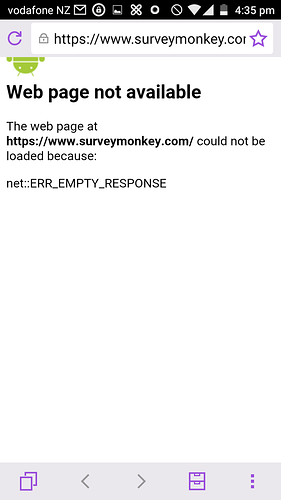
Android:
“net::ERR_EMPTY_RESPONSE”
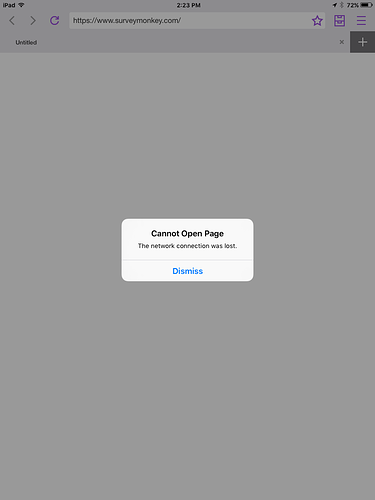
iOS:
“Cannot open page The network connection was lost”
Running a traffic capture while replicating the issue revealed issue happening at server hello.
Instead of receiving a server hello we would get a “Handshake Failure”
In our case we use netscaler 10.5 with WorxWeb 10.2 utilising Secure Browse.
Secure Browse works kind of like a reverse proxy, WorxWeb connects to netscaler and in turn netcaler establishes a new SSL connection to the requested resource.
Here is an article by F5 on troubleshooting SSL handshake failures https://support.f5.com/kb/en-us/solutions/public/15000/200/sol15292.html
Due to the place the handshake failure occurred it is very likely a cipher mismatch.
Running an SSL labs test against SurveyMonkey (https://www.ssllabs.com/ssltest/analyze.html?d=surveymonkey.com) reveals the following
Cipher Suites (SSL 3+ suites in server-preferred order; deprecated and SSL 2 suites at the end)
TLS_ECDHE_RSA_WITH_AES_256_GCM_SHA384 (0xc030) ECDH secp256r1 (eq. 3072 bits RSA) FS 256
TLS_ECDHE_RSA_WITH_AES_128_GCM_SHA256 (0xc02f) ECDH secp256r1 (eq. 3072 bits RSA) FS 128
TLS_ECDHE_RSA_WITH_AES_256_CBC_SHA384 (0xc028) ECDH secp256r1 (eq. 3072 bits RSA) FS 256
TLS_ECDHE_RSA_WITH_AES_256_CBC_SHA (0xc014) ECDH secp256r1 (eq. 3072 bits RSA) FS 256
TLS_ECDHE_RSA_WITH_3DES_EDE_CBC_SHA (0xc012) ECDH secp256r1 (eq. 3072 bits RSA) FS 112
TLS_ECDHE_RSA_WITH_AES_128_CBC_SHA256 (0xc027) ECDH secp256r1 (eq. 3072 bits RSA) FS 128
TLS_ECDHE_RSA_WITH_AES_128_CBC_SHA (0xc013) ECDH secp256r1 (eq. 3072 bits RSA) FS 128
While if we look at the Client Hello sent by the netscaler we can see that none of these ciphers are offered, therefore as guessed earlier it is a cipher mismatch.
Cipher Suites (32 suites)
Cipher Suite: TLS_RSA_WITH_RC4_128_MD5 (0x0004)
Cipher Suite: TLS_RSA_WITH_RC4_128_SHA (0x0005)
Cipher Suite: TLS_RSA_EXPORT_WITH_RC4_40_MD5 (0x0003)
Cipher Suite: TLS_RSA_WITH_DES_CBC_SHA (0x0009)
Cipher Suite: TLS_RSA_WITH_3DES_EDE_CBC_SHA (0x000a)
Cipher Suite: TLS_RSA_EXPORT_WITH_DES40_CBC_SHA (0x0008)
Cipher Suite: TLS_RSA_EXPORT1024_WITH_RC4_56_SHA (0x0064)
Cipher Suite: TLS_RSA_EXPORT1024_WITH_RC4_56_MD5 (0x0060)
Cipher Suite: TLS_RSA_EXPORT1024_WITH_RC2_CBC_56_MD5 (0x0061)
Cipher Suite: TLS_RSA_EXPORT_WITH_RC2_CBC_40_MD5 (0x0006)
Cipher Suite: TLS_DHE_DSS_WITH_RC4_128_SHA (0x0066)
Cipher Suite: TLS_DHE_DSS_EXPORT1024_WITH_RC4_56_SHA (0x0065)
Cipher Suite: TLS_DHE_DSS_EXPORT1024_WITH_DES_CBC_SHA (0x0063)
Cipher Suite: TLS_RSA_WITH_AES_128_CBC_SHA (0x002f)
Cipher Suite: TLS_RSA_WITH_AES_256_CBC_SHA (0x0035)
Cipher Suite: TLS_DHE_RSA_WITH_DES_CBC_SHA (0x0015)
Cipher Suite: TLS_DHE_RSA_WITH_3DES_EDE_CBC_SHA (0x0016)
Cipher Suite: TLS_DHE_RSA_EXPORT_WITH_DES40_CBC_SHA (0x0014)
Cipher Suite: TLS_DHE_RSA_WITH_AES_128_CBC_SHA (0x0033)
Cipher Suite: TLS_DHE_RSA_WITH_AES_256_CBC_SHA (0x0039)
Cipher Suite: TLS_DHE_DSS_WITH_DES_CBC_SHA (0x0012)
Cipher Suite: TLS_DHE_DSS_WITH_3DES_EDE_CBC_SHA (0x0013)
Cipher Suite: TLS_DHE_DSS_EXPORT_WITH_DES40_CBC_SHA (0x0011)
Cipher Suite: TLS_DHE_DSS_WITH_AES_128_CBC_SHA (0x0032)
Cipher Suite: TLS_DHE_DSS_WITH_AES_256_CBC_SHA (0x0038)
Cipher Suite: TLS_DH_anon_WITH_RC4_128_MD5 (0x0018)
Cipher Suite: TLS_DH_anon_WITH_DES_CBC_SHA (0x001a)
Cipher Suite: TLS_DH_anon_WITH_3DES_EDE_CBC_SHA (0x001b)
Cipher Suite: TLS_DH_anon_EXPORT_WITH_RC4_40_MD5 (0x0017)
Cipher Suite: TLS_DH_anon_EXPORT_WITH_DES40_CBC_SHA (0x0019)
Cipher Suite: TLS_DH_anon_WITH_AES_128_CBC_SHA (0x0034)
Cipher Suite: TLS_DH_anon_WITH_AES_256_CBC_SHA (0x003a)
Looking through Citrix documentation on netscaler 10.5 the ECDHE ciphers are only supported for front end communication (in this case we use backend as netscaler is acting as a client).
http://docs.citrix.com/en-us/netscaler/10-5/ns-tmg-wrapper-10-con/ns-ssl-wrapper-con-10/ns-ssl-supported-ciphers-list-ref.html
However looking at documentation for netscaler 11 the ECDHE ciphers are part of the default cipher suit
http://docs.citrix.com/en-us/netscaler/11/traffic-management/ssl/supported-ciphers-list-release-11.html
Therefore it looks like the solution to this issue is to upgrade netscaler to version 11.